Cyber Security
Stay Ahead with Cybersecurity Solutions
Shield Your Business from Cyber Threats
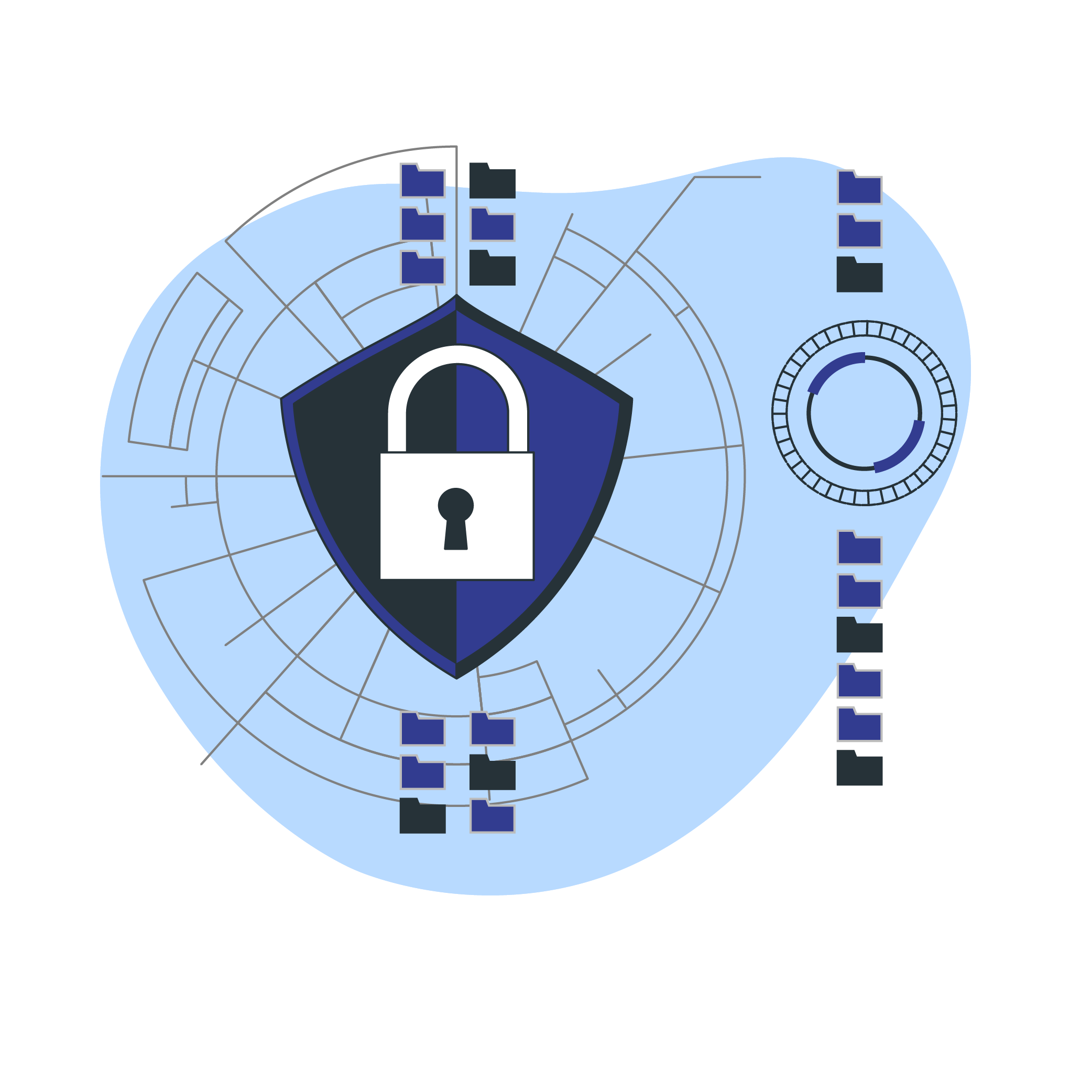















These assessments evaluate threats, vulnerabilities, and their potential consequences to organizational assets. Risk assessments help organizations assess their security posture, identify problem areas, prioritize risks based on likelihood and severity, and devise a plan for remediation.
IR is a structured process for detection, analysis, containment, eradication, and recovery from a security breach. Precise execution of IR plans minimizes the potential for damage caused by an incident. In lieu of an existent plan, use of third-party IR services can be arranged to mitigate a cyber incident in progress.
Vulnerability scans help organizations identify security gaps in defenses and prioritize remediation plans. Regular assessment of system weaknesses and potential targets of attack, using both automated and manual scanning techniques, ensures comprehensive vulnerability identification.
Also known as pentesting, this is the simulation of real-world cyberattacks to uncover vulnerabilities in the organization’s security posture. Penetration testing takes many forms, from black-box testers with no prior knowledge of the target, to a planned offensive by “red team” adversaries with predefined objectives and goals.
These services protect individual information and identities by detecting potentially fraudulent activity through credit report morning and dark web surveillance. They commonly include identity restoration services to remediate any issues uncovered.
Implementation of access management services ensures that only authorized users can access sensitive information. Using multi-factor authentication (MFA) secures accounts by requiring multiple forms of identity verification for access, while single sign-on (SSO) simplifies user access by requiring just one login credential for authentication into multiple applications.
MSS are outsourced security services that offer 24/7 security monitoring and protection for businesses that lack adequate resources or expertise to manage security operations. They often depend on an advanced cybersecurity platform to consolidate and coordinate security efforts. MSS enables organizations to rapidly scale their security capabilities while reducing expenses and operational costs.
Awareness training educates users on threats and security best practices, raising awareness to encourage a culture of security and minimize security errors that result in incidents. Regular cybersecurity training may include advice on secure authentication, proper data handling, and phishing attacks simulations


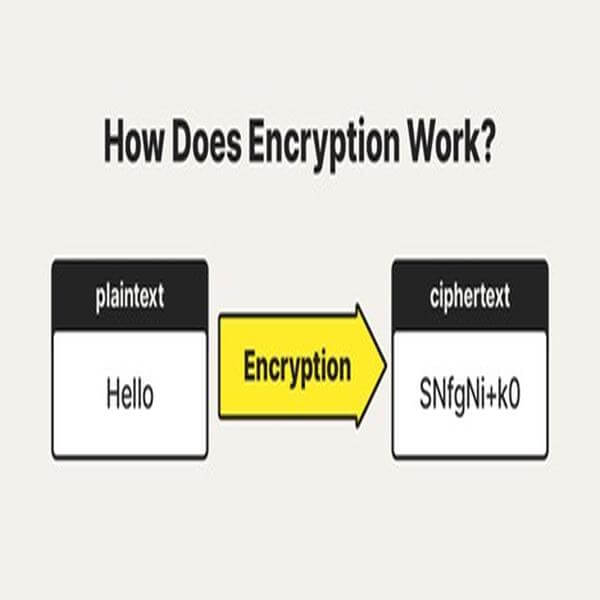
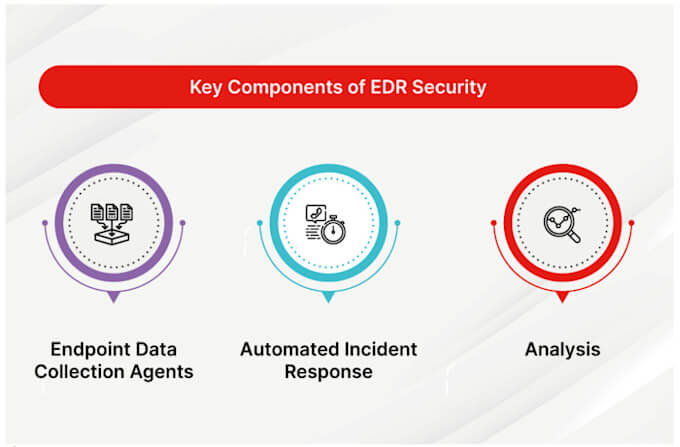
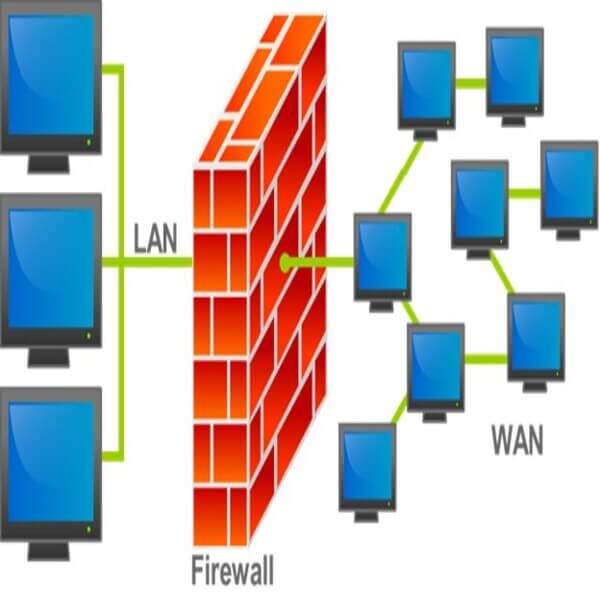







Cybersecurity services protect organizations from a wide range of threats, from hazards like infrastructure vulnerabilities and unauthorized account access, to active security breaches in progress.
Discover the power of AI to transform your business operations, boost efficiency, and drive innovation.